One of the key steps in protecting yourself online is to determine if you’ve been “pwned” – a term used to describe when your personal information has been compromised or leaked in a data breach. This article will guide you through the process of finding out if you’ve been pwned and provide valuable insights to protect your sensitive information.
How to Find Out If You’ve Been Pwned
What Does “Pwned” Mean?
Before diving into the methods to check if you’ve been pwned, let’s first clarify what “pwned” actually means. The term originated from a typographical error, where the “p” key is located adjacent to the “o” key on a keyboard, a form of leetspeak. When a player defeats an opponent effortlessly in an online game, the opponent is said to have been “pwned” instead of “owned.” In the context of cybersecurity, being “pwned” means that your personal information has been compromised or exposed due to a data breach.
Here’s how you can use HIBP to find out if you’ve been pwned:
Visit the Have I Been Pwned website
Access the HIBP website by typing https://haveibeenpwned.com into your web browser’s address bar.
Enter your email address
On the HIBP homepage, you’ll find a search bar. Enter your primary email address or any other email address you suspect may have been compromised.
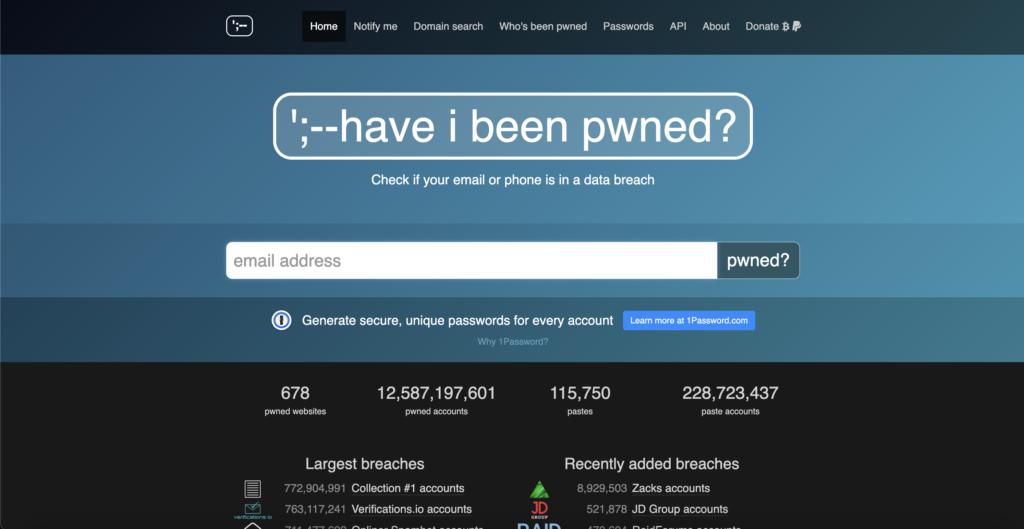
Review the results
Once you hit enter, HIBP will provide you with a detailed report of any data breaches associated with the email address you entered. If your email address has been pwned, it’s crucial to take immediate action to secure your accounts.
Take necessary precautions
If HIBP indicates that your email address has been compromised, change the password for the affected account immediately. Furthermore, ensure that you’re not using the same password for multiple accounts, as this can increase your vulnerability to further attacks.
By utilizing HIBP, you can quickly identify if your personal information has been compromised and take appropriate steps to mitigate the risks.
Protecting Your Digital Identity
Now that you know how to find out if you’ve been pwned, it’s essential to take proactive measures to protect your digital identity. Here are some best practices to safeguard your personal information from cyber threats:
Strong and Unique Passwords
Creating strong and unique passwords is the first line of defense against cyber attacks. Avoid using common or easily guessable passwords, such as “password123” or “123456.” Instead, develop complex passwords that include a combination of uppercase and lowercase letters, numbers, and special characters.
Use a generator to create strong and unique passwords and save them to your password manager. 1Password has a generator built-in, though you don’t even need the service to have access to a great password generator.
Password Managers
Managing multiple strong passwords can be a daunting task. Password managers are tools that securely store your passwords and automatically fill them in when needed. They offer convenience while ensuring that you’re using unique and robust passwords for each online account.
1Password is known for its exceptional security and ease of use. It offers a seamless experience across multiple devices and platforms. With features like password generation, secure storage, and the ability to store other sensitive information, 1Password ensures your data remains protected. It also supports features like two-factor authentication and biometric login.
If you use 1Password at work, you may be able to get a free family plan.
Versatile password manager that prioritizes simplicity and security. It offers password generation, autofill functionality, secure note storage, and a built-in digital wallet for online payments. Dashlane also includes a feature that alerts you if any of your accounts have been compromised in a data breach.
Open-source password manager that provides a secure and transparent solution for managing passwords. It offers cross-platform compatibility, password syncing, secure storage, and password generation. Bitwarden’s free version is robust, while the premium version adds additional features like advanced two-factor authentication options.
A comprehensive password manager that emphasizes strong encryption and security features. It offers a user-friendly interface, password generation, secure storage, and the ability to share passwords securely. Keeper also includes features like secure file storage and encrypted messaging.
Steer clear of products like LastPass due to multiple, recent data breaches of their own.
Two-Factor Authentication (2FA)
Enable two-factor authentication whenever possible. This adds an extra layer of security by requiring an additional verification step, such as a temporary code sent to your mobile device, when logging into your accounts. Even if your password is compromised, hackers will still need physical access to your second factor to gain entry.
Regularly Update Software
Keep your operating system, web browsers, and other software up to date. Software updates often include important security patches that address vulnerabilities and protect against the latest threats.
Be Cautious of Phishing Attempts
Phishing is a common tactic used by cybercriminals to trick individuals into revealing their sensitive information. Be wary of unsolicited emails, messages, or phone calls that request personal information or contain suspicious links. Always verify the authenticity of the source before providing any confidential data.
Monitor Your Accounts
Regularly monitor your online accounts for any suspicious activity. Check your bank statements, credit reports, and other financial records to ensure there are no unauthorized transactions. If you notice any discrepancies, report them immediately to the relevant authorities and take necessary action to secure your accounts.
For 1Password users, Watchtower is built into the 1Password app and browser extension.
While you should never store passwords in your browser, you can use Google’s Password Checkup to do a quick HIBP search of your stored passwords. Once done, migrate them to a password manager 🙂
FAQs about Being Pwned
Where does this data come from?
HIBP sources its information from a variety of reliable and reputable sources. The data included in the HIBP database comes from several different channels, all aimed at identifying and tracking data breaches. Here are some of the primary sources from which HIBP obtains its information:
Publicly Disclosed Breaches: Data is collected from breaches that have been publicly disclosed by the organizations affected. When companies announce that they have experienced a data breach, HIBP gathers the relevant information and adds it to the database.
Security Researchers: Ethical hackers and security researchers play a vital role in identifying and reporting data breaches. HIBP collaborates with these experts who discover breaches independently and responsibly disclose them. By working with security researchers, HIBP ensures that the database remains comprehensive and up to date.
Data Sharing Services: HIBP receives data from various data-sharing services. These services allow individuals to anonymously contribute breach data that they have discovered or obtained. This crowd-sourced information helps expand the coverage of the database and provides a wider range of breached accounts.
Third-Party Leaks: In some cases, HIBP obtains breach data from leaks that have been published on various platforms or shared within underground communities. While these sources need to be handled carefully, they can provide valuable insights into data breaches that would otherwise go unnoticed.
How often should I check if I’ve been pwned?
It’s a good practice to periodically check if you’ve been pwned, especially after high-profile data breaches or if you suspect any unusual account activity. Aim to check at least once every few months to stay proactive in protecting your digital identity.
Can I check multiple email addresses on HIBP?
Absolutely! HIBP allows you to check multiple email addresses to determine if any of them have been compromised. Simply enter each email address into the search bar, one at a time, and review the results accordingly.
What should I do if my email address has been pwned?
If HIBP reveals that your email address has been pwned, it’s crucial to take immediate action. Change the password for the affected account and enable two-factor authentication. Additionally, review your other accounts for any shared or similar passwords and update them to enhance your overall security.
Can I trust Have I Been Pwned?
Absolutely! Have I Been Pwned (HIBP) is widely regarded as a trustworthy and reliable resource within the cybersecurity community. Created by respected security expert Troy Hunt, HIBP has earned a strong reputation for providing accurate and up-to-date information on data breaches.
There are several reasons why I trust HIBP:
Transparency: Operates with utmost transparency, openly sharing its data sources and methodologies. Troy Hunt has been meticulous in documenting the data breaches included in the database, ensuring transparency and accountability in the information provided.
Verification: Sources its data from a variety of reputable sources, including publicly available breach data, security researchers, and individuals who have shared their own findings. Troy Hunt verifies the data to the best of his ability before including it in the database, further bolstering its reliability.
Track Record: Has been in operation since 2013 and has continuously updated its database with new breaches. Over the years, it has gained the trust of millions of users and has been endorsed by numerous cybersecurity professionals and organizations.
Recognition: Troy Hunt, the creator of HIBP, is a well-known and respected figure in the cybersecurity industry. His expertise and contributions to the field have been widely recognized, and he has received accolades for his work on raising awareness about data breaches and promoting cybersecurity best practices.
Third-Party Verification: HIBP’s data has been independently verified by various organizations and researchers. It has been used as a reliable source for identifying compromised accounts and breached data in numerous investigations and research studies.
Are there alternatives to HIBP?
While HIBP is an excellent resource, there are alternative services available for checking if you’ve been pwned. Some notable alternatives include BreachAlarm, SpyCloud, and Firefox Monitor. Each of these services operates slightly differently, so you may want to explore them to find the one that best suits your needs.
In reality, Have I Been Pwned’s API likely powers most of the services and integrations available in the market.
Is it possible to completely eliminate the risk of being pwned?
While it’s challenging to completely eliminate the risk of being pwned, following best practices and staying vigilant can significantly reduce your vulnerability. By adopting strong passwords, using two-factor authentication, and regularly monitoring your accounts, you can minimize the potential impact of data breaches.
As Google, Apple, and other tech companies and developers implement passkeys, passwords as we know them will slowly fade away, offering a much more secure way of signing in to the services you use every day.
Some services allow the use of passkeys on Google Chrome, Android, iOS, and macOS. 1Password has opened up a beta program for its passkeys feature.








