Understanding the TagDiv Plugin Vulnerability
The TagDiv plugin, renowned for its versatility in enhancing WordPress website functionalities, recently came under the spotlight due to a critical vulnerability. Once exploited by malicious actors, this flaw grants unauthorized access to WordPress sites, paving the way for various forms of cyberattacks such as data breaches, defacement, and malware injection. Exploiting this vulnerability has already compromised numerous WordPress sites worldwide, underscoring the urgency for comprehensive mitigation strategies.
Exploitation Techniques and Implications
Malicious entities exploit the TagDiv plugin vulnerability through various techniques, including but not limited to SQL injection, cross-site scripting (XSS), and remote code execution (RCE). By leveraging these techniques, attackers can gain unrestricted access to sensitive data, manipulate site content, and execute arbitrary code within the WordPress environment. The ramifications of such exploits extend beyond immediate financial losses to include reputational damage, legal repercussions, and regulatory non-compliance.
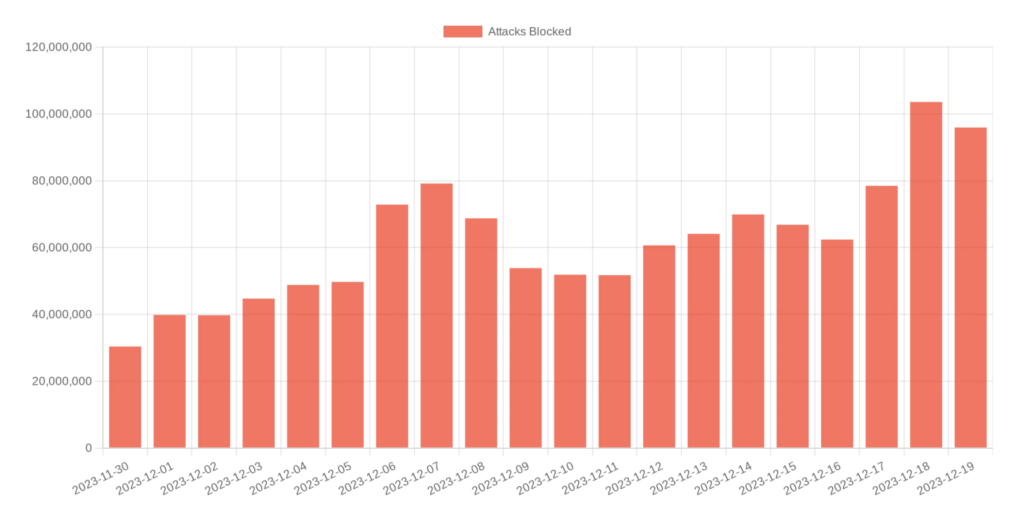
WordPress security firm Malcare reportedly blocked over 1.2 billion XSS attempts aimed at td-composer in December.
Mitigation Strategies
Patch Immediately
The foremost step in mitigating the risks associated with the TagDiv plugin vulnerability is to ensure the timely application of patches released by the plugin developer. These patches address the underlying security flaws, thereby fortifying the plugin against exploitation attempts. Website administrators are advised to regularly monitor for plugin updates and promptly install them to mitigate potential risks.
Implement Web Application Firewalls (WAFs)
Deploying a robust Web Application Firewall (WAF) is an additional defense layer against malicious traffic targeting the TagDiv plugin vulnerability. WAFs analyze incoming web requests, intercepting and blocking malicious payloads before they reach the WordPress site. Administrators can effectively reduce the risk of successful attacks by configuring WAFs to filter out known exploit patterns associated with the TagDiv vulnerability.
Conducting Regular Security Audits
Regular security audits are pivotal in identifying and addressing potential vulnerabilities within the WordPress environment, including plugins such as TagDiv. By leveraging automated scanning tools and manual inspection techniques, website administrators can proactively detect and remediate security weaknesses before they are exploited by malicious actors.
Enforcing the Principle of Least Privilege
Adhering to the principle of least privilege entails restricting user privileges and access rights within the WordPress ecosystem to minimize the potential impact of security breaches. Administrators can limit the attack surface and mitigate the consequences of compromised user accounts by assigning permissions based on functional necessity and implementing stringent access controls.





